Hello, this is Hermes Solution.
This week’s blog explores the two core pillars of automotive safety: cybersecurity (ISO/SAE 21434) and functional safety (ISO 26262).
In today’s automotive industry, cybersecurity and functional safety can no longer be treated as separate disciplines. As vehicles become increasingly connected and autonomous, cyberattacks are evolving from simple data breaches into direct threats to human life.
As of 2024, more than 95% of vehicle cyberattacks are executed remotely, revealing a new class of risks introduced by connectivity and wireless interfaces.
This article explains how “Threats” (under ISO/SAE 21434) and “Hazards” (under ISO 26262) are interrelated and why both standards must be addressed together throughout the vehicle development lifecycle.
ISO/SAE 21434: Understanding “Threats” from a Cybersecurity Perspective
ISO/SAE 21434 defines the automotive cybersecurity management framework across the entire vehicle lifecycle—from concept and design to production, operation, and decommissioning.
A Threat is defined as a potential malicious act that could cause harm to a system or organization.
For example, if an attacker infiltrates an ECU (Electronic Control Unit) or communication channel and manipulates data or injects false control commands, they could directly influence steering or braking functions—transforming a cybersecurity issue into a safety incident.
Core Elements of a Cybersecurity Threat
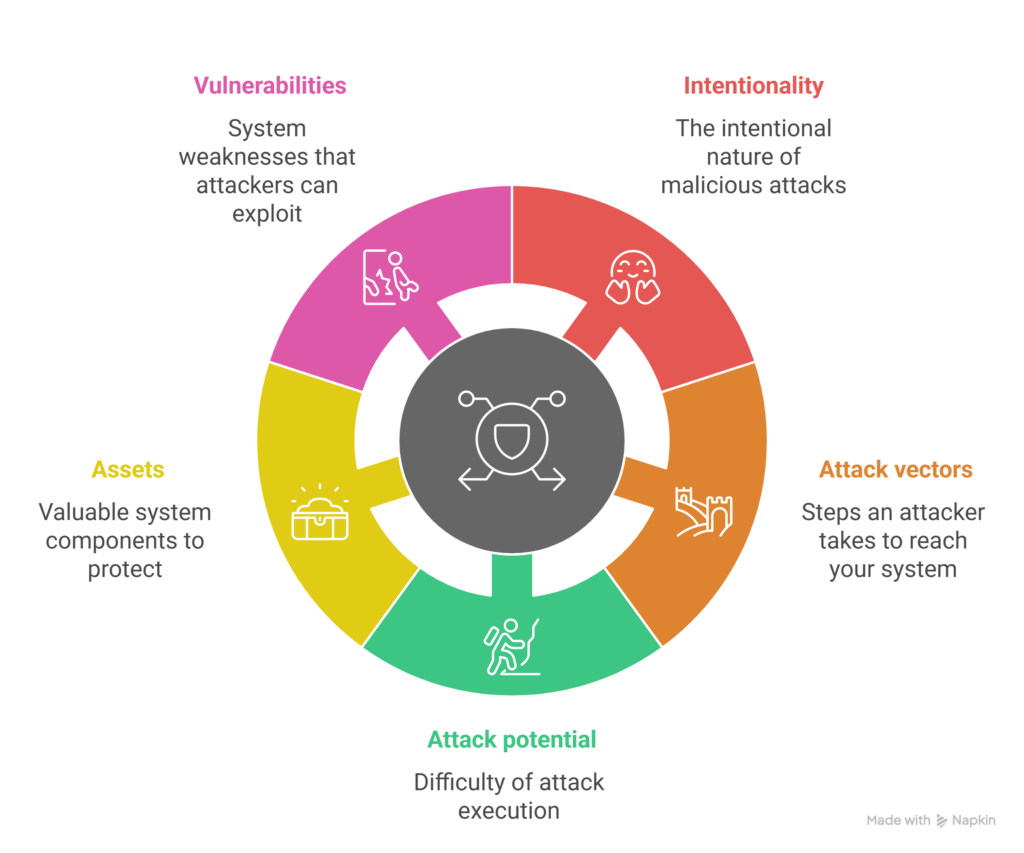
Intentionality: The threat originates from a deliberate, malicious human act—not accidental system failure.
Attack Path: The route an attacker takes to reach the target system.
Example: External Network → Gateway ECU → Internal CAN Bus → Braking ECUAttack Feasibility: Difficulty of execution based on required time, skill, equipment, and access.
Asset: Anything that must be protected, such as ECUs, communication channels, encryption keys, or firmware code.
Vulnerability: Weaknesses that an attacker could exploit, such as poor encryption, faulty authentication, or open ports.
ISO/SAE 21434 evaluates threats based on the CIA Triad:
Confidentiality – Prevent unauthorized data access
Integrity – Ensure data and functions cannot be modified arbitrarily
Availability – Ensure the system operates when needed
The required protection level is expressed as CAL (Cybersecurity Assurance Level, 1–4):
Level | Risk Level | Assurance Level | Typical Security Measures | Example Systems |
|---|---|---|---|---|
CAL | Low | Basic protection | Access control, basic authentication | Infotainment, diagnostic ports |
CAL 2 | Medium | Standard protection | Encrypted communication, logging, user authentication | OBD interface, vehicle gateway |
CAL 3 | High | Advanced protection | Intrusion detection, integrity checks | ECU-to-ECU communication, OTA update system |
CAL 4 | Very High | Multi-layered defense | HSM, key protection, intrusion prevention | Braking/steering ECUs, ADAS control systems |
ISO 26262: Understanding “Hazards” from a Functional Safety Perspective
ISO 26262 addresses risks caused by malfunctioning E/E systems in vehicles.
A Hazard refers to a potential source of harm resulting from system malfunction or random hardware/software failure.
While cyberattacks are intentional, hazards are unintentional—arising from faults such as sensor failure, logic errors, or unstable power supply.
HARA: Hazard Analysis and Risk Assessment
ISO 26262 uses three key parameters:
Severity (S): Potential level of harm
Exposure (E): Likelihood of encountering the situation
Controllability (C): Driver’s ability to control or mitigate the situation
Combining these factors yields the ASIL (Automotive Safety Integrity Level), ranging from A to D, with D representing the highest integrity level.
Example: Brake failure at highway speed → ASIL D
Fundamental Differences Between Threats and Hazards
Aspect | ISO/SAE 21434 (Threat) | ISO 26262 (Hazard) |
|---|---|---|
Cause | Intentional malicious attack | Random system fault |
Nature of Risk | Adaptive adversary | Statistically predictable failure |
Assessment | TARA (Impact × Attack Feasibility) | HARA (Severity × Exposure × Controllability) |
Integrity Level | CAL 1–4 | ASIL A–D |
Time Dynamics | Continuously evolving | Relatively static |
Focus | Unknown, emerging attacks | Known failure modes |
In essence, Threats intentionally disrupt system operation, while Hazards result from unintentional malfunctions.
However, they are not independent—a cyber threat can become a safety hazard.
How a Threat Becomes a Hazard
Modern research confirms that cyberattacks can trigger safety incidents:
Sensor Data Manipulation: Tampering with radar or camera signals leads to misperception and potential collision.
ECU Control Override: Attackers inject commands that alter braking or steering behavior.
Communication Interference: Disruption of V2V messages causes cooperative driving systems to malfunction.
These cybersecurity threats can escalate into functional safety hazards under ISO 26262, posing immediate physical risks.
Real-World Example: Remote Brake System Attack
In a controlled test, researchers exploited vulnerabilities in a telematics ECU via a 5G network, gaining access to the in-vehicle CAN bus.
They successfully sent forged braking commands, causing the car to stop abruptly without driver input.
Assessment by Standards:
Attack Feasibility: Medium (Skilled attacker within ~1 month effort)
Severity (S): S3 – Life-threatening potential
Exposure (E): E4 – Highway driving is common
Controllability (C): C3 – Driver cannot react
→ ASIL D
This experiment demonstrates how a single cybersecurity breach can directly lead to a functional safety failure—proving that security equals safety.
Comparing TARA and HARA Methodologies
Item | TARA (ISO/SAE 21434) | HARA (ISO 26262) |
|---|---|---|
Target | Cyber threats | System malfunctions |
Key Factors | Impact × Attack Feasibility | Severity × Exposure × Controllability |
Outcome | Cybersecurity goals + CAL | Safety goals + ASIL |
Frequency | Continuous (upon new vulnerabilities) | Event-driven (upon design changes) |
Evaluation | Semi-quantitative | Qualitative |
Both are preventive analyses—TARA anticipates human-driven attacks, whereas HARA models system-driven failures.
Toward Integration: The Rise of HATARA
The industry is now embracing HATARA—an integrated approach combining HARA + TARA to jointly evaluate threats and hazards within one framework.
This unified process aligns ASIL and CAL levels for consistent risk management.
Advantages:
Eliminates duplicate analysis
Ensures consistency between safety and security requirements
Reduces project cost and lead time
Enables holistic system-level risk control
Conclusion: Safety and Security Must Converge

Modern vehicles are software-defined, network-connected systems, making isolated management of safety and security impossible.
A security breach can instantly create a safety risk, merging the two domains in practice and lifecycle management.
The automotive industry is already adopting HATARA and STPA-SafeSec methodologies to unify these disciplines.
Ultimately, the ability to integrate ISO/SAE 21434 and ISO 26262 will determine the reliability and trustworthiness of future mobility systems.
Key Takeaways
Cybersecurity threats are intentional; functional safety hazards are unintentional.
In reality, a single threat can evolve into a hazard.
ISO/SAE 21434 and ISO 26262 must be implemented in tandem.
HATARA will likely become the industry’s de facto standard.
Safety without security is impossible.
This article was prepared by Hermes Solution to emphasize the importance of integrated automotive safety and cybersecurity management.
Hermes continues to provide expert insights on ISO/SAE 21434, ISO 26262, and AI-driven vehicle safety systems.
Design the future of safe mobility with Hermes.